
The Unusual Suspect: Git Repos
While phishing and ransomware dominate headlines, another critical risk quietly persists across most enterprises: exposed Git repositories leaking sensitive data. A risk that silently creates

While phishing and ransomware dominate headlines, another critical risk quietly persists across most enterprises: exposed Git repositories leaking sensitive data. A risk that silently creates

In cybersecurity, precision matters—and there’s little room for error. A small mistake, missed setting, or quiet misconfiguration can quickly lead to much bigger problems. The

India’s Central Bureau of Investigation (CBI) has announced that it has taken steps to dismantle what it said was a transnational cybercrime syndicate that carried

Cybersecurity researchers have discovered a new hacking technique that exploits weaknesses in the eSIM technology used in modern smartphones, exposing users to severe risks. The

NVIDIA is urging customers to enable System-level Error Correction Codes (ECC) as a defense against a variant of a RowHammer attack demonstrated against its graphics
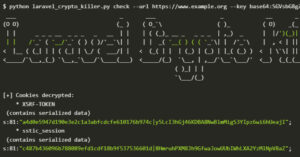
Cybersecurity researchers have discovered a serious security issue that allows leaked Laravel APP_KEYs to be weaponized to gain remote code execution capabilities on hundreds of

Fortinet has released fixes for a critical security flaw impacting FortiWeb that could enable an unauthenticated attacker to run arbitrary database commands on susceptible instances.

Cybersecurity researchers have discovered a set of four security flaws in OpenSynergy’s BlueSDK Bluetooth stack that, if successfully exploited, could allow remote code execution on

An Iranian-backed ransomware-as-a-service (RaaS) named Pay2Key has resurfaced in the wake of the Israel-Iran-U.S. conflict last month, offering bigger payouts to cybercriminals who launch attacks

A recently disclosed maximum-severity security flaw impacting the Wing FTP Server has come under active exploitation in the wild, according to Huntress. The vulnerability, tracked
