
5 Reasons Why Attackers Are Phishing Over LinkedIn
Phishing attacks are no longer confined to the email inbox, with 1 in 3 phishing attacks now taking place over non-email channels like social media,

Phishing attacks are no longer confined to the email inbox, with 1 in 3 phishing attacks now taking place over non-email channels like social media,

This week showed just how fast things can go wrong when no one’s watching. Some attacks were silent and sneaky. Others used tools we trust
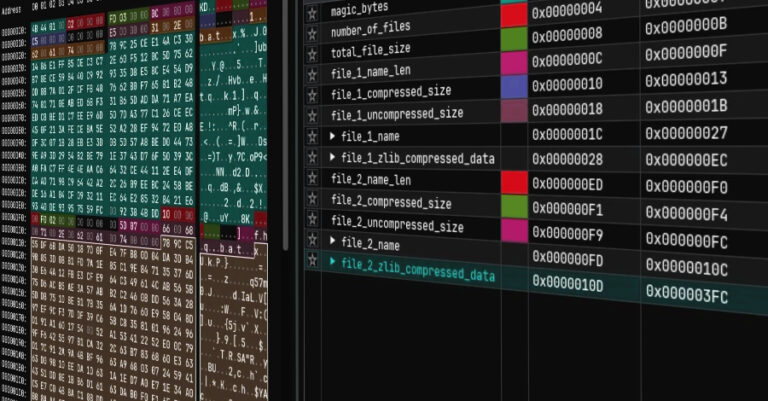
The threat actor known as Dragon Breath has been observed making use of a multi-stage loader codenamed RONINGLOADER to deliver a modified variant of a

Google has disclosed that the company’s continued adoption of the Rust programming language in Android has resulted in the number of memory safety vulnerabilities falling

The botnet malware known as RondoDox has been observed targeting unpatched XWiki instances against a critical security flaw that could allow attackers to achieve arbitrary

The U.S. Department of Justice (DoJ) on Friday announced that five individuals have pleaded guilty to assisting North Korea’s illicit revenue generation schemes by enabling
The North Korean threat actors behind the Contagious Interview campaign have once again tweaked their tactics by using JSON storage services to stage malicious payloads.

The Iranian state-sponsored threat actor known as APT42 has been observed targeting individuals and organizations that are of interest to the Islamic Revolutionary Guard Corps
Cybersecurity researchers have uncovered critical remote code execution vulnerabilities impacting major artificial intelligence (AI) inference engines, including those from Meta, Nvidia, Microsoft, and open-source PyTorch

Key Takeaways: 85 active ransomware and extortion groups observed in Q3 2025, reflecting the most decentralized ransomware ecosystem to date. 1,590 victims disclosed across 85
