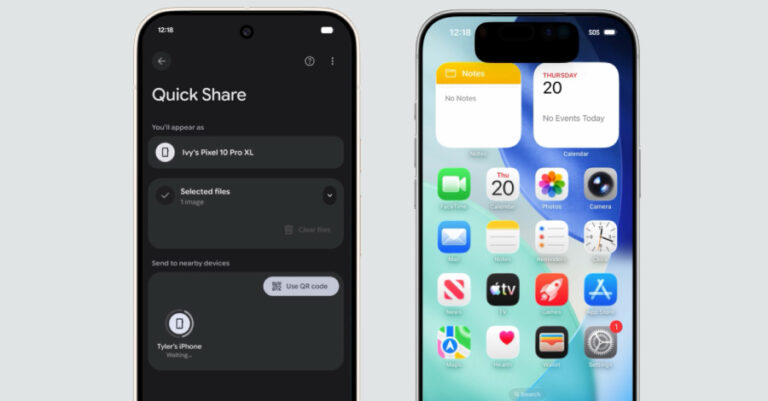
Grafana Patches CVSS 10.0 SCIM Flaw Enabling Impersonation and Privilege Escalation
Grafana has released security updates to address a maximum severity security flaw that could allow privilege escalation or user impersonation under certain configurations. The vulnerability,