
From Impact to Action: Turning BIA Insights Into Resilient Recovery
Modern businesses face a rapidly evolving and expanding threat landscape, but what does this mean for your business? It means a growing number of risks,

Modern businesses face a rapidly evolving and expanding threat landscape, but what does this mean for your business? It means a growing number of risks,

North Korean threat actors have been attributed to a coordinated cyber espionage campaign targeting diplomatic missions in their southern counterpart between March and July 2025.

A 22-year-old man from the U.S. state of Oregon has been charged with allegedly developing and overseeing a distributed denial-of-service (DDoS)-for-hire botnet called RapperBot. Ethan
Threat actors are exploiting a nearly two-year-old security flaw in Apache ActiveMQ to gain persistent access to cloud Linux systems and deploy malware called DripDropper.

Financial institutions like trading and brokerage firms are the target of a new campaign that delivers a previously unreported remote access trojan called GodRAT. The

A new exploit combining two critical, now-patched security flaws in SAP NetWeaver has emerged in the wild, putting organizations at risk of system compromise and

After two decades of developing increasingly mature security architectures, organizations are running up against a hard truth: tools and technologies alone are not enough to

The U.K. government has apparently abandoned its plans to force Apple to weaken encryption protections and include a backdoor that would have enabled access to

The maintainers of the Python Package Index (PyPI) repository have announced that the package manager now checks for expired domains to prevent supply chain attacks.
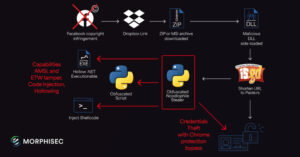
The threat actors behind the Noodlophile malware are leveraging spear-phishing emails and updated delivery mechanisms to deploy the information stealer in attacks aimed at enterprises
