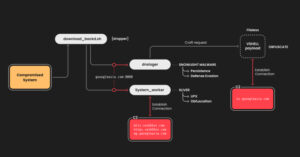
Chinese Hackers Target Linux Systems Using SNOWLIGHT Malware and VShell Tool
The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a known malware dubbed SNOWLIGHT and

The China-linked threat actor known as UNC5174 has been attributed to a new campaign that leverages a variant of a known malware dubbed SNOWLIGHT and

A critical security vulnerability has been disclosed in the Apache Roller open-source, Java-based blogging server software that could allow malicious actors to retain unauthorized access

Everybody knows browser extensions are embedded into nearly every user’s daily workflow, from spell checkers to GenAI tools. What most IT and security people don’t

The North Korea-linked threat actor assessed to be behind the massive Bybit hack in February 2025 has been linked to a malicious campaign that targets
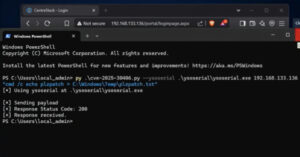
A recently disclosed security flaw in Gladinet CentreStack also impacts its Triofox remote access and collaboration solution, according to Huntress, with seven different organizations compromised
Meta has announced that it will begin to train its artificial intelligence (AI) models using public data shared by adults across its platforms in the

Cybersecurity researchers have discovered a new, sophisticated remote access trojan called ResolverRAT that has been observed in attacks targeting healthcare and pharmaceutical sectors. “The threat

Cybersecurity researchers are calling attention to a new type of credential phishing scheme that ensures that the stolen information is associated with valid online accounts.

Attackers aren’t waiting for patches anymore — they are breaking in before defenses are ready. Trusted security tools are being hijacked to deliver malware. Even

AI is changing cybersecurity faster than many defenders realize. Attackers are already using AI to automate reconnaissance, generate sophisticated phishing lures, and exploit vulnerabilities before
copyright ©2025 centrynex
