Anthropic Launches Claude Code Security for AI-Powered Vulnerability Scanning
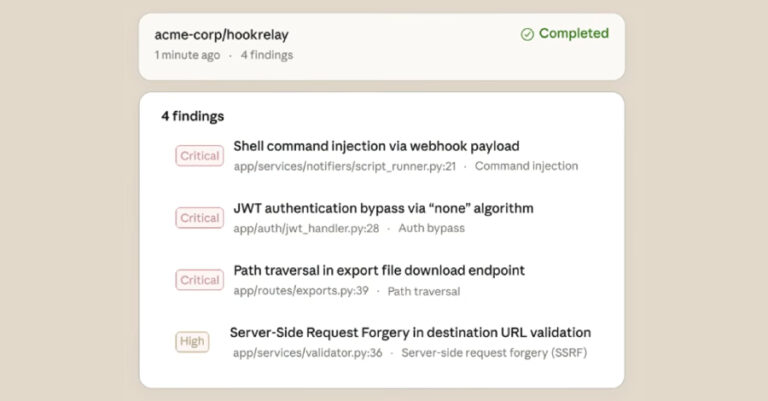
Artificial intelligence (AI) company Anthropic has begun to roll out a new security feature for Claude Code that can scan a user’s software codebase for

Artificial intelligence (AI) company Anthropic has begun to roll out a new security feature for Claude Code that can scan a user’s software codebase for

Threat actors have been observed exploiting a recently disclosed critical security flaw impacting BeyondTrust Remote Support (RS) and Privileged Remote Access (PRA) products to conduct

In yet another software supply chain attack, the open-source, artificial intelligence (AI)-powered coding assistant Cline CLI was updated to stealthily install OpenClaw, a self-hosted autonomous

Cybersecurity researchers have disclosed details of a new ClickFix campaign that abuses compromised legitimate sites to deliver a previously undocumented remote access trojan (RAT) called

A 29-year-old Ukrainian national has been sentenced to five years in prison in the U.S. for his role in facilitating North Korea’s fraudulent information technology

With one in three cyber-attacks now involving compromised employee accounts, insurers and regulators are placing far greater emphasis on identity posture when assessing cyber risk.

The U.S. Federal Bureau of Investigation (FBI) has warned of an increase in ATM jackpotting incidents across the country, leading to losses of more than

Two former Google engineers and one of their husbands have been indicted in the U.S. for allegedly committing trade secret theft from the search giant

Microsoft has disclosed a now-patched security flaw in Windows Admin Center that could allow an attacker to escalate their privileges. Windows Admin Center is a

An international cybercrime operation against online scams has led to 651 arrests and recovered more than $4.3 million as part of an effort led by
