
Artificial Intelligence – What’s all the fuss?
Talking about AI: Definitions Artificial Intelligence (AI) — AI refers to the simulation of human intelligence in machines, enabling them to perform tasks that typically

Talking about AI: Definitions Artificial Intelligence (AI) — AI refers to the simulation of human intelligence in machines, enabling them to perform tasks that typically

Blockchain is best known for its use in cryptocurrencies like Bitcoin, but it also holds significant applications for online authentication. As businesses in varying sectors
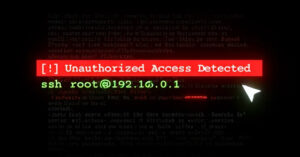
A critical security vulnerability has been disclosed in the Erlang/Open Telecom Platform (OTP) SSH implementation that could permit an attacker to execute arbitrary code sans
Microsoft is calling attention to an ongoing malvertising campaign that makes use of Node.js to deliver malicious payloads capable of information theft and data exfiltration.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) on Wednesday added a security flaw impacting SonicWall Secure Mobile Access (SMA) 100 Series gateways to its
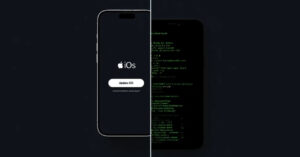
Apple on Wednesday released security updates for iOS, iPadOS, macOS Sequoia, tvOS, and visionOS to address two security flaws that it said have come under

Cybersecurity researchers have detailed four different vulnerabilities in a core component of the Windows task scheduling service that could be exploited by local attackers to

Google on Wednesday revealed that it suspended over 39.2 million advertiser accounts in 2024, with a majority of them identified and blocked by its systems

Threat actors are leveraging an artificial intelligence (AI) powered presentation platform named Gamma in phishing attacks to direct unsuspecting users to spoofed Microsoft login pages.

Introduction Cyber threats targeting supply chains have become a growing concern for businesses across industries. As companies continue to expand their reliance on third-party vendors,
copyright ©2025 centrynex
