
New MacSync macOS Stealer Uses Signed App to Bypass Apple Gatekeeper
Cybersecurity researchers have discovered a new variant of a macOS information stealer called MacSync that’s delivered by means of a digitally signed, notarized Swift application

Cybersecurity researchers have discovered a new variant of a macOS information stealer called MacSync that’s delivered by means of a digitally signed, notarized Swift application

The fraudulent investment scheme known as Nomani has witnessed an increase by 62%, according to data from ESET, as campaigns distributing the threat have also

Every year, cybercriminals find new ways to steal money and data from businesses. Breaching a business network, extracting sensitive data, and selling it on the

The U.S. Securities and Exchange Commission (SEC) has filed charges against multiple companies for their alleged involvement in an elaborate cryptocurrency scam that swindled more

Apple has been fined €98.6 million ($116 million) by Italy’s antitrust authority after finding that the company’s App Tracking Transparency (ATT) privacy framework restricted App

Cybersecurity researchers have discovered two malicious Google Chrome extensions with the same name and published by the same developer that come with capabilities to intercept
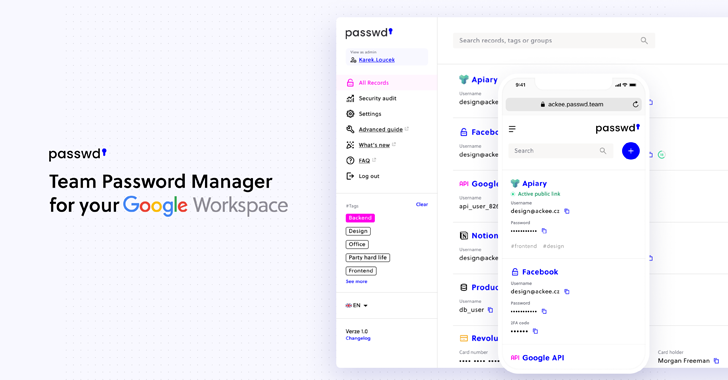
Passwd is designed specifically for organizations operating within Google Workspace. Rather than competing as a general consumer password manager, its purpose is narrow, and business-focused:

A law enforcement operation coordinated by INTERPOL has led to the recovery of $3 million and the arrest of 574 suspects by authorities from 19
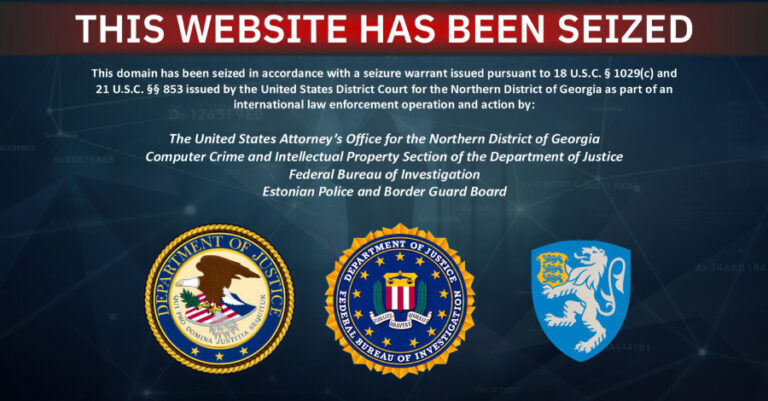
The U.S. Justice Department (DoJ) on Monday announced the seizure of a web domain and database that it said was used to further a criminal

The U.S. Federal Communications Commission (FCC) on Monday announced a ban on all drones and critical components made in a foreign country, citing national security
