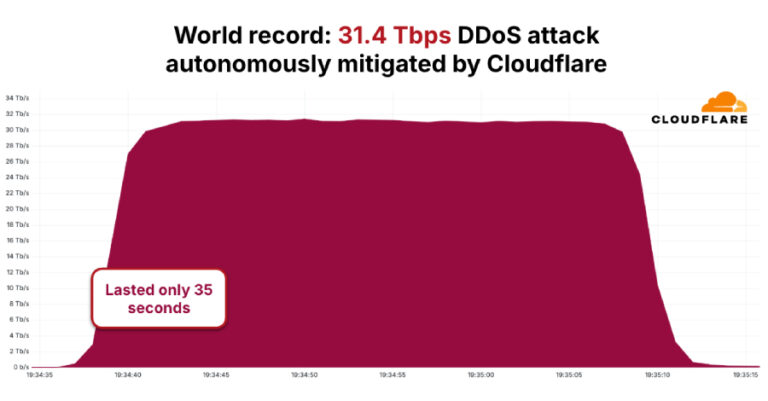
Compromised dYdX npm and PyPI Packages Deliver Wallet Stealers and RAT Malware
Cybersecurity researchers have discovered a new supply chain attack in which legitimate packages on npm and the Python Package Index (PyPI) repository have been compromised