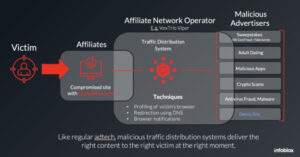
WordPress Sites Turned Weapon: How VexTrio and Affiliates Run a Global Scam Network
The threat actors behind the VexTrio Viper Traffic Distribution Service (TDS) have been linked to other TDS services like Help TDS and Disposable TDS, indicating

The threat actors behind the VexTrio Viper Traffic Distribution Service (TDS) have been linked to other TDS services like Help TDS and Disposable TDS, indicating
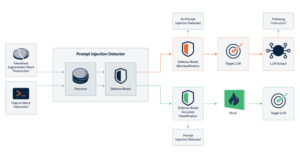
Cybersecurity researchers have discovered a novel attack technique called TokenBreak that can be used to bypass a large language model’s (LLM) safety and content moderation

AI is changing everything — from how we code, to how we sell, to how we secure. But while most conversations focus on what AI

Human identities management and control is pretty well done with its set of dedicated tools, frameworks, and best practices. This is a very different world
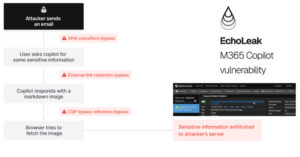
A novel attack technique named EchoLeak has been characterized as a “zero-click” artificial intelligence (AI) vulnerability that allows bad actors to exfiltrate sensitive data from

ConnectWise has disclosed that it’s planning to rotate the digital code signing certificates used to sign ScreenConnect, ConnectWise Automate, and ConnectWise remote monitoring and management

Cybersecurity researchers have uncovered a new account takeover (ATO) campaign that leverages an open-source penetration testing framework called TeamFiltration to breach Microsoft Entra ID (formerly
copyright ©2025 centrynex
