Researchers Demonstrate How MCP Prompt Injection Can Be Used for Both Attack and Defense
As the field of artificial intelligence (AI) continues to evolve at a rapid pace, new research has found how techniques that render the Model Context

As the field of artificial intelligence (AI) continues to evolve at a rapid pace, new research has found how techniques that render the Model Context

Cybersecurity researchers have shed light on a Russian-speaking cyber espionage group called Nebulous Mantis that has deployed a remote access trojan called RomCom RAT since
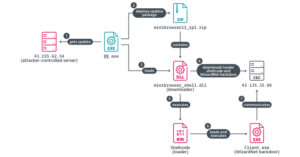
A China-aligned advanced persistent threat (APT) group called TheWizards has been linked to a lateral movement tool called Spellbinder that can facilitate adversary-in-the-middle (AitM) attacks.

How Many Gaps Are Hiding in Your Identity System? It’s not just about logins anymore. Today’s attackers don’t need to “hack” in—they can trick their

Cybersecurity researchers have revealed that RansomHub’s online infrastructure has “inexplicably” gone offline as of April 1, 2025, prompting concerns among affiliates of the ransomware-as-a-service (RaaS)

Everyone has cybersecurity stories involving family members. Here’s a relatively common one. The conversation usually goes something like this: “The strangest thing happened to my
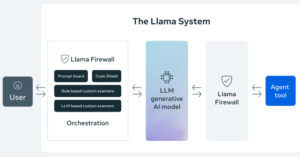
Meta on Tuesday announced LlamaFirewall, an open-source framework designed to secure artificial intelligence (AI) systems against emerging cyber risks such as prompt injection, jailbreaks, and

A high court in the Indian state of Karnataka has ordered the blocking of end-to-end encrypted email provider Proton Mail across the country. The High
copyright ©2025 centrynex
